As increasingly more of our regular routines move the internet, getting our associated gadgets and computerized trails has become progressively significant. While routers often include basic firewall capabilities out of the box, setting up a robust network firewall can provide an extra layer of protection. Enter the Raspberry Pi - with a little tinkering, this tiny computer is perfectly capable of serving as a firewall appliance, screening traffic and locking down your local network.
In this guide, we'll explore how to configure a Raspberry Pi to act as a network firewall using OpenWrt or IPTables. You'll learn about basic firewall concepts, assess your security needs, and get the step-by-step instructions to build and manage your own Pi firewall. By the end, your network will be better guarded from threats both inside and outside your home.
Get Free PCB Assembly
Firewall Fundamentals
Before we dive into configuring the Pi, it's helpful to understand some core firewall principles. A firewall acts as a barrier, regulating traffic flowing in and out of a network. It uses rules, also called policies or filters, to determine whether packets are allowed to cross the barrier or not.
There are a few main types of firewalls:
- Packet Filtering Firewalls - Examine headers of IP packets to filter traffic based on things like source/destination addresses and ports. IPTables is an example.
- Stateful Packet Inspection Firewalls - Track the state of network connections and only allow traffic that follows protocol-specific guidelines. OpenWrt offers this.
- Application Layer Firewalls - Monitor content within application layer protocols to filter network traffic based on application layer data like URLs, viruses/malware payloads, etc. More advanced.
In general, firewalls are useful not just for blocking outside threats but also controlling connectivity between internal devices and segments. They add another guard to the Castle walls so to speak - allowing networking while protecting privacy and security.
Choosing Setup Method
A few popular ways to set up a Raspberry Pi firewall include:
- IPTables: The standard Linux kernel firewall, run manually or via scripts. Lightweight but requires technical know-how.
- Firewalld: User-friendly front-end for configuring Netfilter/IPtables firewall rules on Linux/Unix. Part of Raspberry Pi OS.
- OpenWrt: Linux distribution optimized for embedded devices with robust built-in firewall UI. Full-fledged router firmware.
- Pi-hole: Network-wide ad blocking through DNS filtering at the network edge. Acts somewhat like a limited firewall too.
Which you choose depends on needs and skill level. IPTables is basic but customizable, Firewalld and OpenWrt have full-fledged web interfaces for lay users, and Pi-hole focuses solely on blocking unwanted domains.
With Raspberry Pis being so affordable, using one for each approach is also an option for learning. Start simple and graduate to more robust implementations later as requirements grow.
Preparing the Pi
First, install the latest version of Raspberry Pi OS (formerly Raspbian) on a microSD card and boot it up. Raspberry Pi OS comes with IPTables pre-configured, making it ready for firewall tasks right away.
Connect the Pi to your router/switch via Ethernet and log into its IP address in a web browser to access its built-in configuration interface. Here are some initial steps:
- Change the default password for security. Enable SSH for remote access.
- Update all software with sudo apt update && sudo apt upgrade. Keep the system patched.
- Create a firewall user account with restricted sudo privileges for security tasks.
- Back up your work with sudo rpi-backup in case you need to re-image the SD card.
Now you're ready to dive into building out the firewall! Choose from IPTables, Firewalld, or OpenWrt based on needs.
IPTables Firewall on Raspbian
IPTables is the built-in firewall software of Linux. To get started:
- Become root or use sudo. Run iptables -L to list the current firewall rules.
- Flush existing rules with iptables -F. Now you have a blank slate.
- Allowloopback traffic with iptables - An Information - I lo - j Acknowledge.
- Use iptables to acknowledge associations that have proactively been laid out: -An Information - m state - - state Laid out, RELATED - j Acknowledge.
- Deny all other traffic with iptables -P INPUT DROP. Traffic will now be blocked by default.
- Save rules with iptables-save > /etc/iptables.rules. Reload on reboot.
- Use iptables -I INPUT -p tcp --dport 80 -j ACCEPT to whitelist ports individually as needed.
You now have a basic IPTables firewall blocking all traffic! Tweak rules as desired. The Linux iptables website has tons more options to refine policies.
OpenWrt Router Firmware
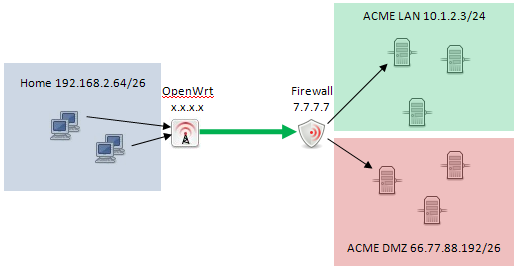
Setup
For a more full-featured firewall experience, try deploying OpenWrt on the Pi:
- Download the latest OpenWrt image from openwrt.org for your Pi model.
- Flash it to an SD card using Etcher. Reboot.
- Connect to the Pi's IP via browser. Set Username/Password.
- Go to Security > Firewall and click Enable Firewall. Accept Established is on.
- Use Services, Traffic Shaper, UCI scripts for port forwarding, QoS etc.
- Click Add under Firewall Zone to create custom rules blocking/allowing IPs or ports between LAN/WAN.
- Configure WiFi security, DHCP server and more via the full OpenWrt web interface.
OpenWrt turns the Pi into a true versatile firewall router with loads of configuration options for blocking malware and securing your IoT devices on the network too. Try customizing it further with packages.
Using FirewallD on Raspbian
As an alternative to IpTables, FirewallD provides a user-friendly interface:
- Install with sudo apt install firewalld.
- Enable and start FirewallD with sudo systemctl enable --now firewalld
- List available zones with sudo firewall-cmd --get-zones.
- View active rules with sudo firewall-cmd --list-all.
- Open ports by zone, e.g. sudo firewall-cmd --zone=public --add-port=80/tcp --permanent.
- Reload firewall with sudo firewall-cmd --reload for changes to take effect.
- Use the firewall-cmd utility to manage complex rulesets across zones/interfaces.
- FirewallD's zone-based configuration aims to simplify access control compared to raw IPTables. Explore its features like rich rule classification and connection tracking integration.
Get Instant PCB Online Quote
Additional Firewall Tools
Beyond the core firewall implementations, a Raspberry Pi also enables creatively locking down access through supplementary tools. Consider also trying:
- Squid Proxy: Transparent caching proxy filtering web traffic. Block ads/malware domains.
- Snort IDS: Deploy intrusion detection rules for examining traffic in real-time. Alert on anomalies.
- DHCP/DNS Server: Provide network services from the Pi with additional filtering layers.
- Network Monitoring: Analyze firewall logs, activity on separate interfaces with Wireshark, NtopNG.
- Traffic Shaping: Use packages like Trickle or TC to prioritize/throttle bandwidth usage.
- MAC Spoof Protection: Prevent devices impersonating others on the network.
- VPN Server: Stand up OpenVPN or WireGuard for secure external/remote access to LAN.
- Network Segregation: Utilize VLANs to isolate IoT, guest, or sensitive devices securely.
A Pi can therefore scale to handle diverse networking tasks safely in addition to basic packet filtering functions when combined thoughtfully.
Ongoing Management
Once set up, ongoing firewall management involves monitoring logs, updating rules, and auditing security regularly:
- Review logs for policy violations or intrusion attempts with 'journalctl -xe' or a dedicated log analyzer.
- Back up configuration files, like /etc/iptables.rules, for restoration in case of faults.
- Keep rules synchronized across reboots by configuring scripts to run on system start.
- Test rules by intentionally trying to breach them to check defenses hold up as intended.
- Audit services and close unnecessary open ports to minimize exposed attack surface over time.
- Stay current by keeping OS and software updated using monitoring scripts or a manual routine.
Proactive maintenance helps ensure your Pi firewall defenses remain calibrated optimally over the long run. Check in periodically as your needs and threats evolve too.
In Summary
By running IPTables, Firewalld, OpenWrt or other tools on a Raspberry Pi, you gain a low-cost yet powerful firewall appliance custom-tailored to your unique network requirements. From blocking ads and known malware domains to segregating IoT devices and locking down system ports, a Pi firewall brings an extra layer of control and protection. With a little setup, yours can be guarding your digital Castle perimeter in no time!
Advanced Raspberry Pi Firewall Configurations and Uses
- Physical Security: Discuss ways to physically secure the Pi firewall device, such as enclosure locking, hidden placement, device disabling measures if tampered with.
- Traffic Inspection: Demonstrate how to use tools like tcpdump for Wireshark on the Pi to analyze firewall logs, sniff network activity for troubleshooting.
- Security Hardening: Guide on additional steps like disabling unused services/daemons, disabling password logins, app control for least privilege, OS updates.
- Advanced Routing: How to configure static routing, network address translation (NAT), route filtering, packet mangling for stricter traffic control.
- Failsafe Options: Cover options for firewall high availability/failover using redundant Pis, automatic reboot scripts, remote logging for uptime.
- Directory Services: Explain how to integrate the Pi firewall with external AD/LDAP user auth for authenticated secure access.
- Captive Portals: Instructions for hosting firewall-integrated guest portals for visitor device compliance checks.
- VPN Concentrator: Turn the Pi into an OpenVPN/WireGuard VPN server endpoint for remote access or site-to-site links.
- Guest WiFi Network: Configure a side WiFi SSID behind the firewall for untrusted guest devices in isolation.
- IDS/IPS Rules: Deploy Snort/Suricata intrusion detection signatures to proactively block exploits.
- Encrypted Traffic Handling: Tips for allowing local device access to HTTPS sites while still blocking external threats.
Deeper Dives into Select Advanced Topics
Physical Security
- Enclosures to hide the Pi and secure cables/ports from tampering. Motion sensors for unauthorized access.
- Tamper-evident locks/seals to detect if the case has been opened. Disabling iptables rules if physical tamper is detected.
- Monitored power supplies that cut power if disconnected to prevent theft of the device.
Advanced Routing
- Using policy routing/rule tables to selectively route traffic between VLANs or WAN/LAN based on protocol, source/destination etc.
- Static routes to define specific paths for traffic rather than relying on dynamic routing protocols.
- Route filters to restrict propagation of routes and control routing behavior.
- Network Address Translation (NAT) for masquerading/port forwarding to allow accessing internal servers from outside.
Failsafe Options
- Heartbeat scripts to monitor firewall health and restart processes if unresponsive. Alerting if restarts happen.
- Firewall clustering using Carnegie Mellon University's Trickle project to load balance and achieve high availability.
- Geographic load balancing across multiple firewalls in different locations for redundancy.
- Out of band management using cellular dongles as backup connection for remote administration if LAN is down.
Directory Services
- Step-by-step guide on integrating with open source solutions like FreeIPA for centralized auth against an LDAP/Kerberos server.
- Filter network access based on group policies and permissions from an AD server. Simplified large network management.
Free Components Worldwide Shipping
FAQ
Q: Can a regular home router be used as a firewall instead of a Raspberry Pi?
A: Yes, many home routers already include basic firewall features. However, using a Raspberry Pi provides more customization options and control. It also allows pairing additional security tools that consumer routers may not support.
Q: How do I access the Raspberry Pi firewall remotely when away from home?
A: You can SSH into the Pi from anywhere once you've enabled remote access. Alternatively, set up a VPN server on the Pi to create an encrypted tunnel back to your network. Or forward ports through your router's firewall and use a remote terminal app. But avoid exposing it directly to the public internet for best security.
Q: What is the difference between IPTables, FirewallD and OpenWrt?
A: IPTables is the fundamental Linux firewall, FirewallD gives a simpler connection point to designing IPTables rules, and OpenWrt is an undeniable switch working framework. IPTables is most customizable but complex, FirewallD simplifies some tasks, and OpenWrt adds extra routing functionality.
Q: How do I view and troubleshoot firewall logs?
A: Use the journalctl command to view logs from Raspbian's journal, or log analyzing tools like Logwatch, Fail2ban, or Snort. You can also use sniffing utilities like tcpdump to analyze actual traffic for debugging.
Q: Is a Raspberry Pi powerful enough to handle my home network traffic load?
A: For most small home networks, a Raspberry Pi will be sufficient as a software firewall. However, if you have very high bandwidth usage or numerous concurrent connections, a more powerful firewall device may be better suited to avoid bottlenecks. Test performance based on your needs.
Q: What other open source firewall distributions could I use besides OpenWrt?
A: Some other popular ones include pfSense, IPFire, Smoothwall Express and Untangle. These provide full-fledged firewall operating systems similar to OpenWrt but with different available packages and configurations.
You may also be interested in...
- How to connect your Raspberry Pi to your computer via Ethernet
- How to SSH Into a Raspberry Pi?
- Free Worldwide Shipping on Over 600,000 Electronics Components with HQ Online
- Free PCB Assembly Offer is Now Live: Experience Reliable PCB Assembly from HQ NextPCB
- HQ NextPCB Introduces New PCB Gerber Viewer: HQDFM Online Lite Edition


